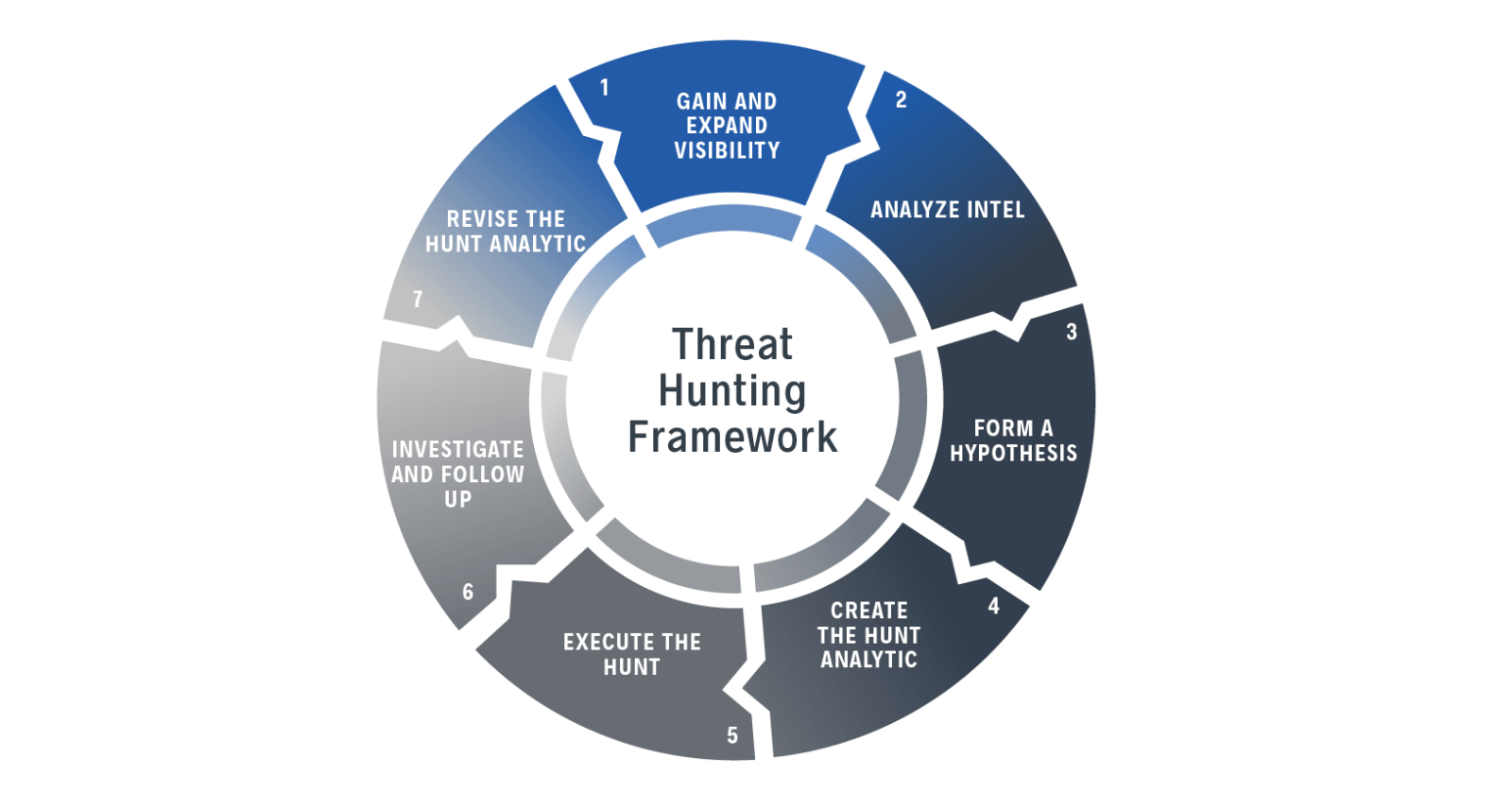
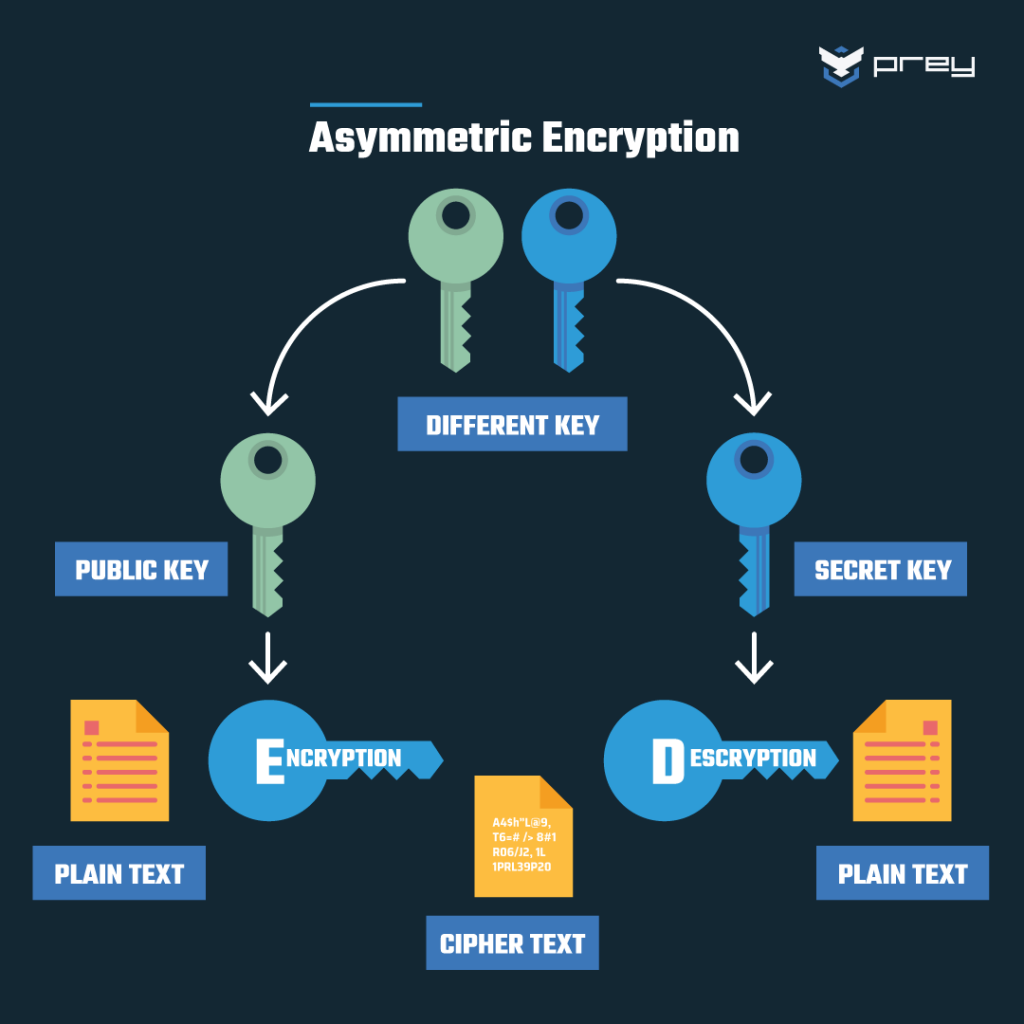
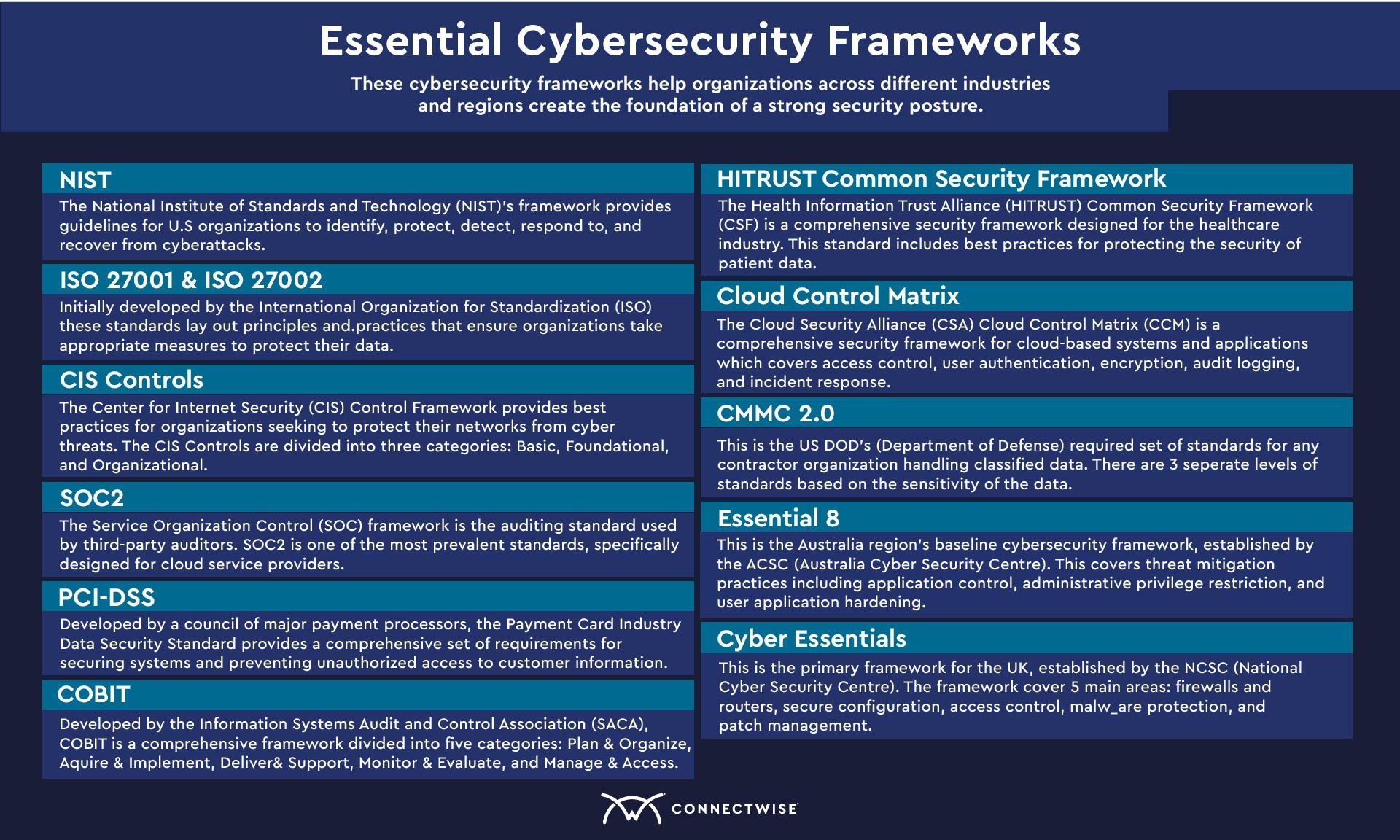
AI-Driven Security Solutions: Enhancing Cyber Protection for Your Business
AI-Driven Security Solutions: Enhancing Cyber Protection for Your Business. Discover how AI-driven security solutions are revolutionizing safety. Explore smart tech that protects your home and business with ease and efficiency! Importance of AI-Driven Security Solutions The integration of AI-Driven Security Solutions: Enhancing Cyber Protection for Your Business is essential for today’s organizations. Cyber threats grow … Read more